Search by the «computer» tag
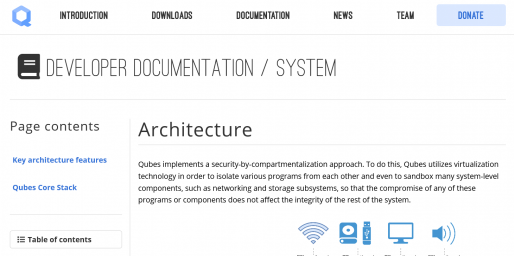
The internet’s initial design, which relied on the end-to-end framework principle, led to mobilization of program specific logic and complexity to the peripheral parts of the network, while keeping the network’s center focusing on the simple task of delivery of data.More
Welcome to My Support & Hard Work I'm offering you a good service. I can ship to your address safely many stuff, for example, Phones or Laptops and many more.... I'm also good at Ebay Carding, so i can card you what you want up to 10 000$ real value daily. I can card all ebay : ebay.co.uk, ebay.in, ebay.com, ebay.More
We are a group of expert & professional hackers, carders from all over the world, who has developed skills from the shadows of dark web & deepweb with hidden services, Our primary goal is to give you safe and secure proficient hacking and financial services.More
Quantum’s (a.k.a. Guanzhong Chen) blog about coding, security, and other computer technology.More
hy, physics, sociology, algorithms, artificial intelligence, big data, cloud, computer, computer architecture, computer graphics, computer hardware, computer network, cryptography, data estructure, database, digital systems, operating system, programming, security, software testing...More
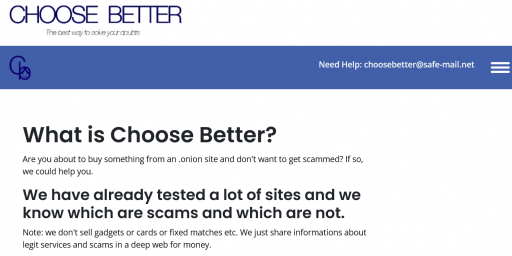
Choose Better tells you whether a .onion site is scam or not Are you about to buy something from an .onion site and don't want to get scammed? If so, we could help you. We have already tested a lot of sites and we know which are scams and which are not.More
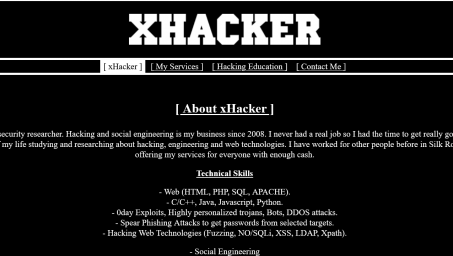
Hire a Hacker, Security Researcher, Offensive Security Web Expert (OSWE), Penetration Tester, Social Engineer. -- Hacking web servers, computers and smartphones. Social Media hacking. Change grades in schools and universities. Information gathering. Exploits, Trojans, RATs, Keyloggers. SQL injections, DoS attacks, Phishing attacks.More
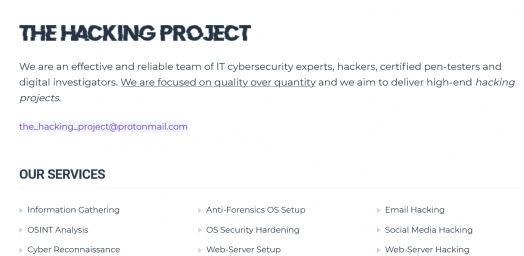
We are an effective and reliable team of IT cybersecurity experts, hackers, certified pen-testers and digital investigators. We are focused on quality over quantity and we aim to deliver high-end hacking projects.More
Hire a hacker for espionage, ruining people, DDOS, hacking, exploits, email or facebook password hack and more. Hacking, Hack, Computer, Spying, Surveillance, Keylogger,DDoS, Tracking,Fraud, Spyware, botnet, Cyber, Extortion, Remove, Hacker, ruining, hackingMore
![[ h4ck3r ] Hacking Services [ h4ck3r ] Hacking Services](../../upload/000/u1/e/4/h4ck3r-hacking-services-photo-normal.png)